JHSC Home / Products / Holland Shielding Home / Data Center Security
Data Center Security
Information Technology Management
Data centers are subject to four threats that are usually overlooked; these are forms of Radiation-Based Data Destruction (RBDD)
Active systems like EMP burst devices
A portable, battery-powered EMP burst device can generate extremely powerful magnetic-field waves for a few milliseconds, comparable to a nuclear electromagnetic pulse (NEMP). One such burst can be enough to damage all servers and other (safety) electronics in your location.
On the internet you can easily find instructions for making an EMP burst device. A handyman can construct one in a few hours with commonly available components. For people who have difficulty reading the texts, there is even an instruction video on YouTube.
And a lazy or less technically skilled criminal can rent a portable device, fully anonymous, for less than US $ 1000, from several sources all over the world. It is a real industry, an entirely new type of crime.
These NEMP waves will propagate through the air for hundreds of meters, and concrete walls are no obstacle. The waves can also travel through existing cables, through the metallic protection around cables or even common pipelines for gas and water, bringing the data-killing power burst to its intended target: your data center.
Military NEMP/EMP
More and more nations and organizations have access to nuclear materials and thus present a risk of nuclear explosions.
To give you an idea of the distances involved: a nuclear burst in the stratosphere above Moscow will create a NEMP field over all of Western Europe, including London. Such a NEMP field can destroy all unprotected data.
Electronic theft
Electronic theft is defined as illegally gathering radiated information by criminals resulting in electronics theft and/or alteration or other manipulation of data.
With sensitive equipment that is currently on the market, data transferred through the air can be read from hundreds of meters away. So in places where a large secured zone cannot be created, like for instance city offices in public buildings, confidential information can be stolen or manipulated.
Solar storms
High levels of solar activity, known as a solar wind shock waves, cause a geomagnetic storm that interacts with the Earth’s magnetic field. This temporary disturbance of the Earth’s magnetosphere can destroy data.
In 1989, a geomagnetic storm energized ground-induced currents that disrupted electric power distribution throughout most of the province of Quebec and caused aurorae as far south as Texas. Another example is the solar storm which only very nearly missed the earth in 2012.
Dangers
New solutions for protecting your data
In collaboration with several universities we have developed, tested and
implemented an electromagnetically shielded Faraday cage for data centers.
With the integrated filtered cables and shielded pipelines, this creates a
radiation-protection wall around your sensible data equipment.
The electromagnetic barrier will withstand any attack or pulse up to a million times.
Features
Protection against:
Summary
Protective measures are no longer the exclusive domain of military, intelligence, forensic and governmental bodies. The high-performance shielding products are available for any company or legal entity taking its data protection seriously.
Together with you, our engineers will work out the optimal solution for your protection needs. We start by making a threat and risk analysis of your data center as the foundation of the Faraday cage protection system.
Active systems like EMP burst devices

Military NEMP/EMP

Electronic theft

Solar storms

Testing
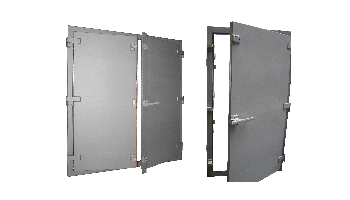
Faraday cages and doors

Shielded Faraday Tent
Shielded vent